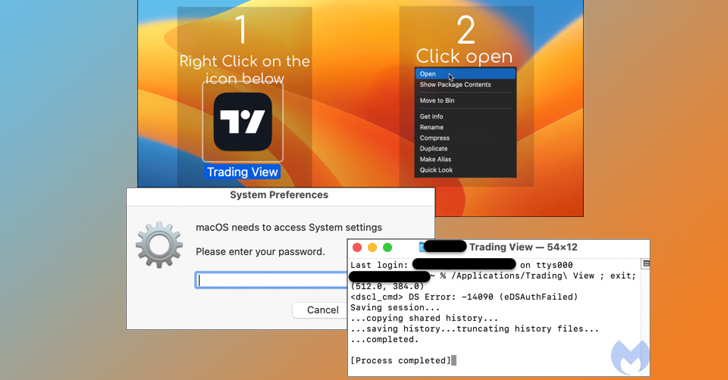
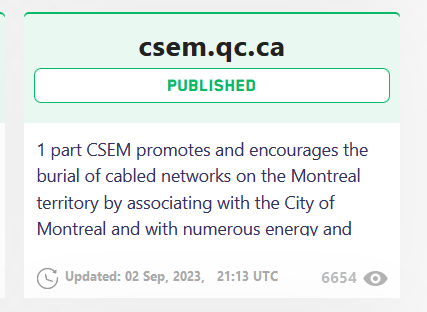
Rhysida Ransomware gang claims to have hacked three more US hospitals

Rhysida Ransomware group added three more US hospitals to the list of victims on its Tor leak site after the PROSPECT MEDICAL attack.
Recently the Rhysida ransomware group made the headlines because it announced the hack of Prospect Medical Holdings …